It looks like iOS & iPadOS 16 support could be coming to the checkm8 bootrom exploit-based palera1n jailbreak a lot sooner than originally anticipated.

It looks like iOS & iPadOS 16 support could be coming to the checkm8 bootrom exploit-based palera1n jailbreak a lot sooner than originally anticipated.
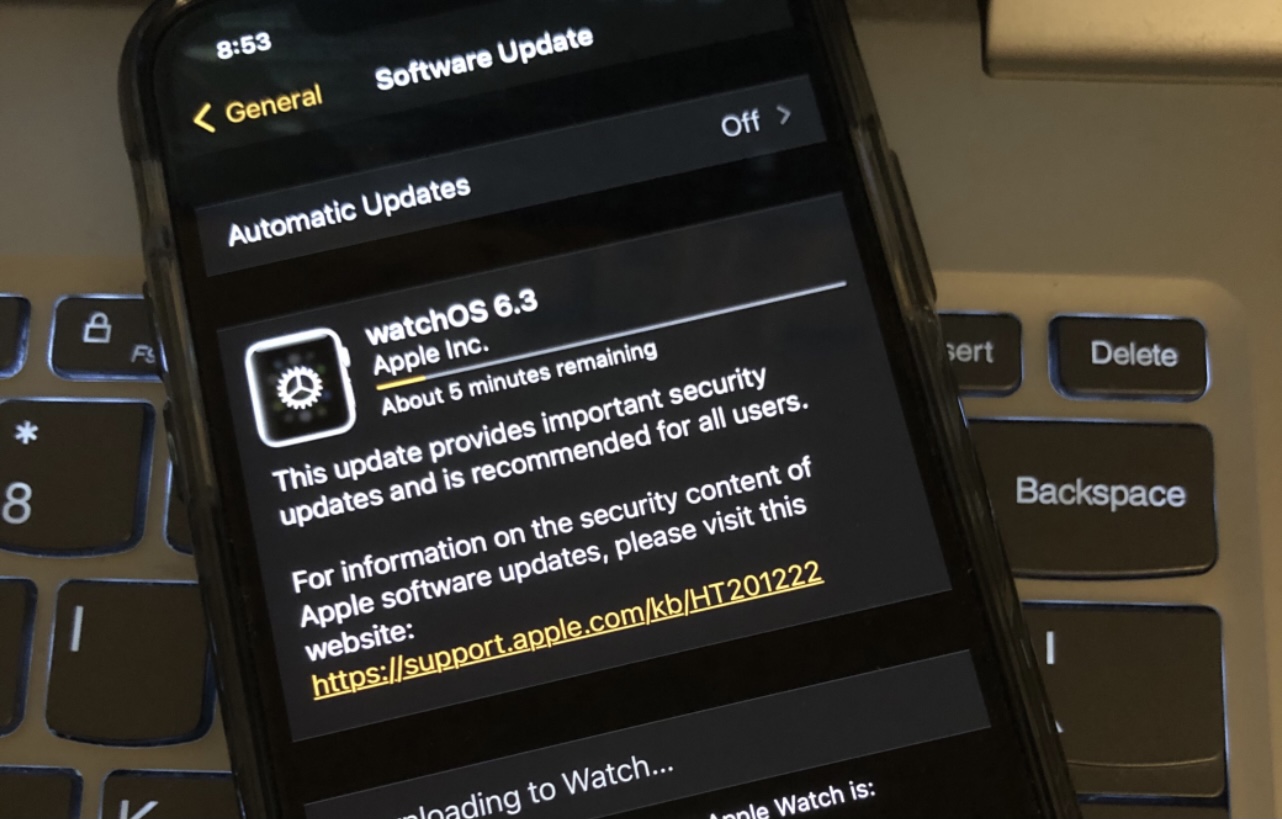
The quest to pwn the Apple Watch is one that has received oodles of attention over the years, and while the concept is most certainly possible, it hasn’t quite reached the level of fruition that most jailbreakers would expect – especially when compared with the jailbreak offerings for iPhones and iPads.
Much of this has to do with the uncertainty of an Apple Watch jailbreak’s usefulness in addition to concerns related to restoring the Apple Watch’s firmware in the event of catastrophic errors (respring loops, etc.), but that hasn’t stopped some jailbreak developers from dabbling with the idea.
It was only a couple of days ago that security researcher Ian Beer shared a rather interesting kernel vulnerability for A11 and older devices (iPhone X and older) running iOS 14.1 and lower. But such a feat begs the question: what about A12 and newer devices?
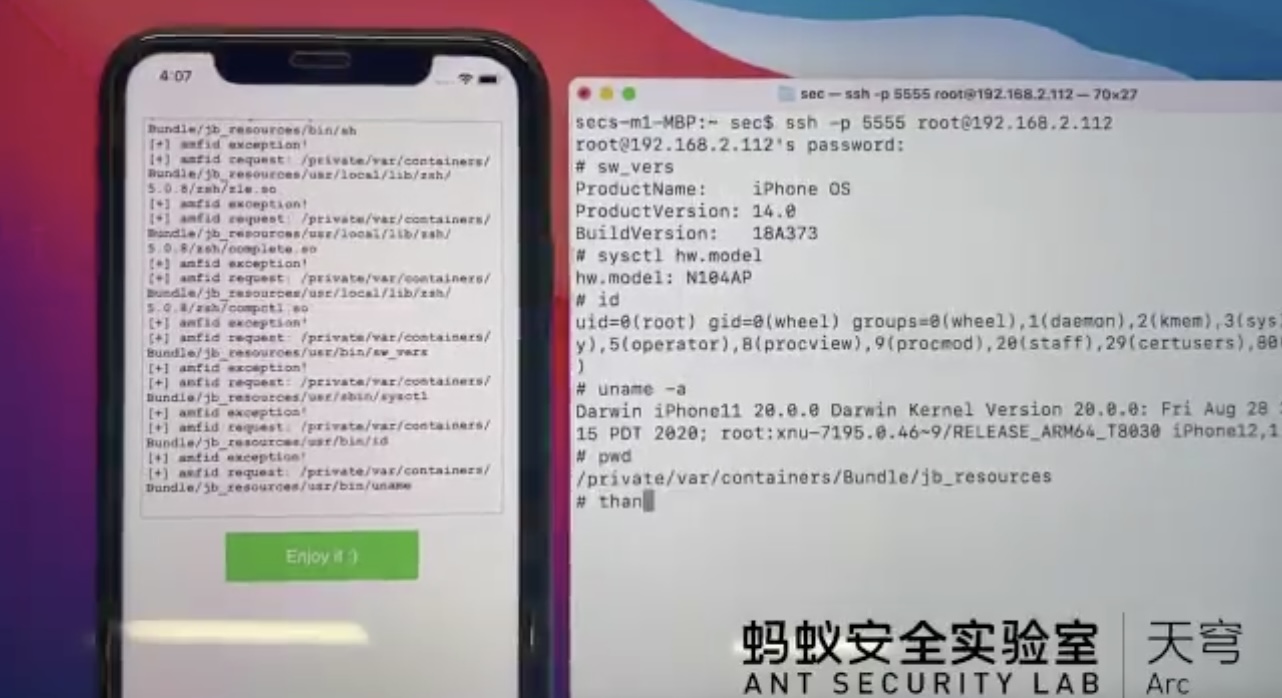
Fortunately for those who’ve been asking this question, there could be a light at the end of the tunnel. Security researcher @pattern_F_ of Ant Security Lab demonstrated what appears to be a successful jailbreak attempt on an iPhone 11 running iOS 14.0
The past few weeks have been crazy for anyone heavily invested in the jailbreak community. Not only was the checkra1n jailbreak updated to add support for A10(X) devices and iOS 14.1-14.2, but a new exploit PoC targeting iOS & iPadOS 13.x was released and FreeTheSandbox once again affirmed that a jailbreak with support for iOS & iPadOS 13.5-13.7 would be released in the near future without a definitive ETA.
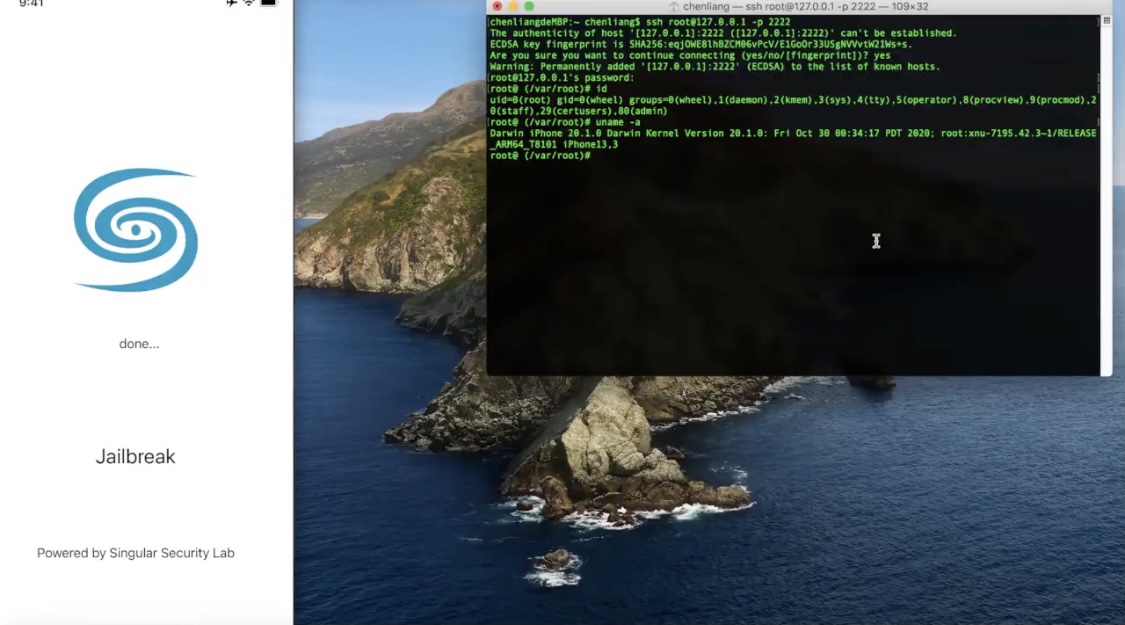
But the community was in for yet another teaser this week after talented security researcher Liang Chen (@chenliang0817) of Singular Security Lab (@SingularSecLab) demonstrated a working jailbreak on Apple’s brand-new iPhone 12 Pro handset running iOS 14.2 — the latest publicly available firmware at the time of this writing:

Apple unleashed iOS & iPadOS 14.2 to the masses yesterday afternoon, and while most iPhone and iPad owners gleefully updated to take advantage of more than 100 new Emojis and six new wallpapers, the updates also appeared to beef up their respective platforms’ security.
Security improvements are generally a good thing for users; however, they can be red flags for proponents of the jailbreak community since software exploits are the very things that make jailbreak tools possible. With that in mind, it may come as no surprise that jailbreak developers repetitiously remind the community to stay in the lowest possible firmware, as this can increase one’s chances of jailbreak eligibility.
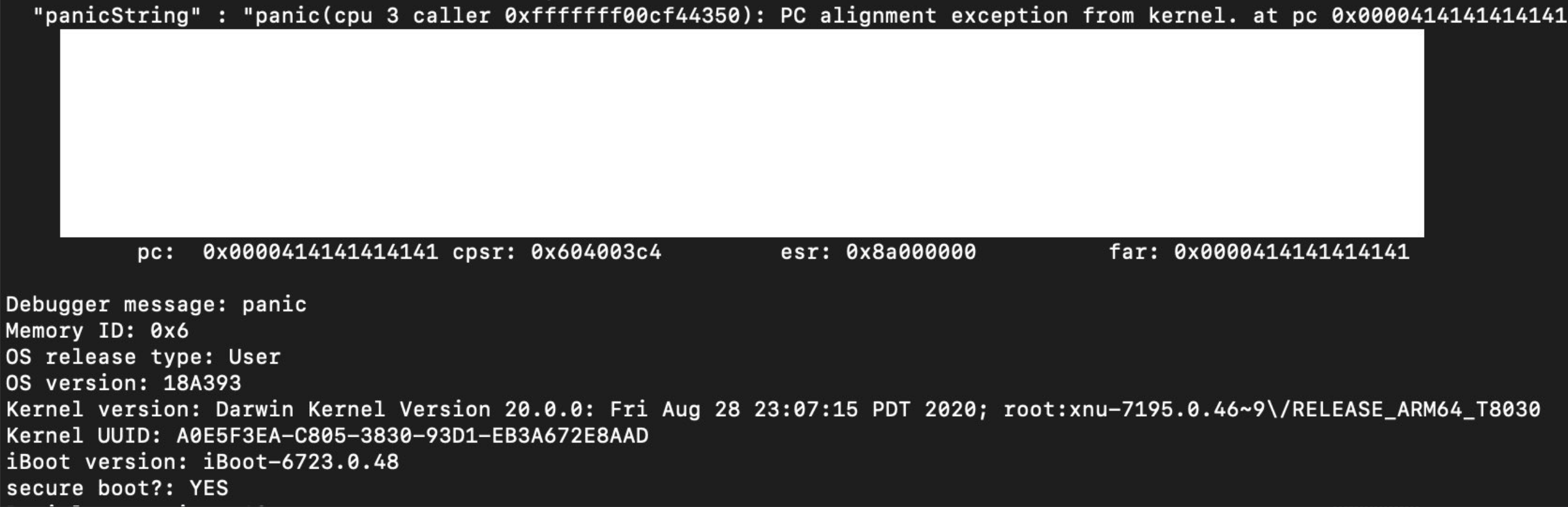
The only iOS & iPadOS 14 devices that can be publicly jailbroken at the time of this writing are those sporting A9 and A9X processors, and while that could change in the very near future as the checkra1n team works on adding A10 and A10X support, the bigger question involves the likes of much newer devices that aren’t even susceptible to the checkm8 bootrom exploit.
Fortunately, renowned hacker and checkra1n team member Luca Todesco shared a particularly interesting announcement via Twitter Monday afternoon in the form of what appears to be a working exploit and PAC bypass for iOS & iPadOS 14 devices:

There’s a certain stigma surrounding jailbreaking and iOS & iPadOS 14 right about now, and all of it stems from the fact that Apple made its latest and greatest mobile operating systems a lot tougher to crack. But tougher doesn’t mean impossible, and that’s a fact, Jack.
With that in mind, it seemed appropriate to follow up with our optimistic attitude following Brandon Azad’s eye-tearing departure from Project Zero with a bit of good news: software security research group ABC Research appears willing to release an iOS & iPadOS 14-compatible exploit to the general public, assuming certain criteria are met…

With Apple dropping software updates for its iPhones and iPads as frequently as they do nowadays, it’s particularly exciting when a hacker claims that they’ve pwned one of the company’s latest versions of iOS and/or iPadOS.
The most recent announcement to shake things up came by way of hacker @08Tc3wBB last month in the form of a new exploit for iOS 13.6.1 that allegedly used a different method to achieve its ends than the more traditional tfp0 method that we see in modern jailbreaks like Odyssey and unc0ver. On Monday, the same hacker appeared to validate that the newer iOS 13.7 would be vulnerable to jailbreak-centric exploitation:
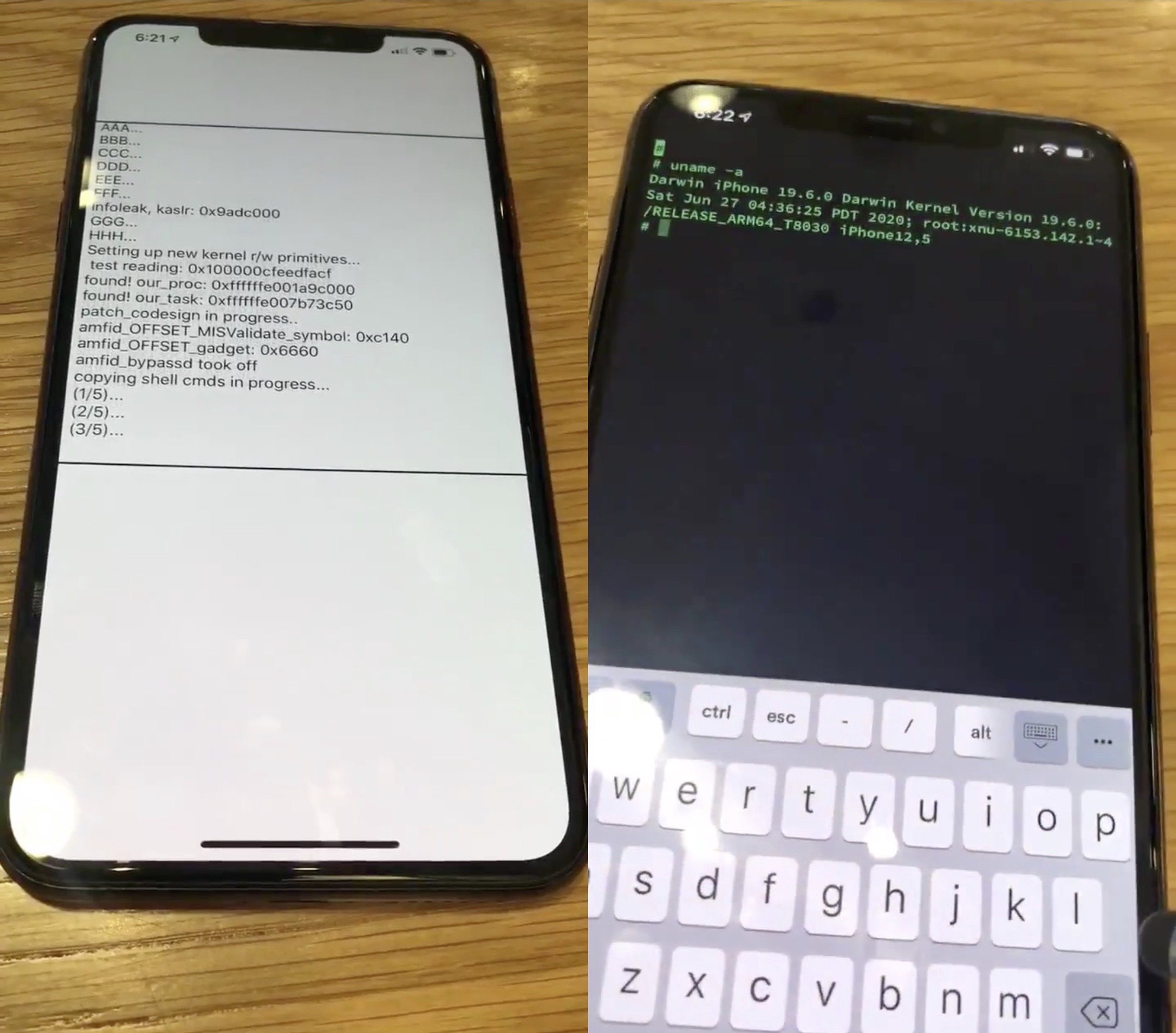
There’s some potentially exciting news for the jailbreak community this weekend after hacker and security researcher @08Tc3wBB teased what appears to be a newfangled approach to exploiting the latest public release of iOS on one of Apple’s current-generation iPhones.
Citing one of @08Tc3wBB’s latest Tweets, it would appear that the hacker successfully pwned an iPhone 11 Pro Max running iOS 13.6.1 without using a traditional tfp0-style exploit like those used in the majority of modern jailbreaks like Odyssey and unc0ver:

When you’re an avid jailbreaker and you hear news about a new exploit that could potentially be used to jailbreak the latest version of iOS, then you tend to get excited about it. This response is only natural, especially given Apple’s rather conspicuous practice of rapidly releasing software updates to patch the very exploits hackers release in order to jailbreak iPhones and iPads alike.
With that in mind, jailbreakers might be particularly thrilled to learn that a new tfp0 exploit has been cooked up for Apple’s brand-new iOS & iPadOS 13.6 release, which was dropped to the public only yesterday afternoon. The news was first shared via Twitter user and security researcher @_Simo36 Thursday morning:

Jailbreakers with access to an A7-A11 device pretty much have it made thanks to the hardware exploit-based checkra1n jailbreak that can’t be patched by Apple in a software update. Those handling newer devices, such as the A12 and A13 varieties, instead depend on infrequently released tfp0 exploits. These seem to surface sporadically with no rhyme or reason, and they can unfortunately be patched by Apple’s software updates.
On a more positive note, it does appear that a skilled security researcher going by the Twitter handle @ProteasWang has achieved tfp0 on an A13-equipped handset running iOS 13.4.1. This is currently the latest version of iOS available from Apple, and with that in mind, the news has particularly exciting implications for jailbreaks such as unc0ver and the to-be-released Chimera13 tool.

It was only yesterday that talented hacker and iOS exploit tinkerer Jake James released time_waste, a reworked version of Brandon Azad’s oob_timestamp tfp0 exploit. Time_waste solves many of the memory leak issues that were present in the oob_timestamp exploit, and given the apparent enhancements, it’s not difficult to see why Pwn20wnd switched to using James’ exploit for the unc0ver jailbreak instead.
But while the aforementioned advantages are obvious, that didn’t stop James from taking things a step further. Just this afternoon, James announced via Twitter that he had managed to get the time_waste tfp0 exploit working on iOS 12; moreover, it even seems to play nicely with A8X-equipped devices: