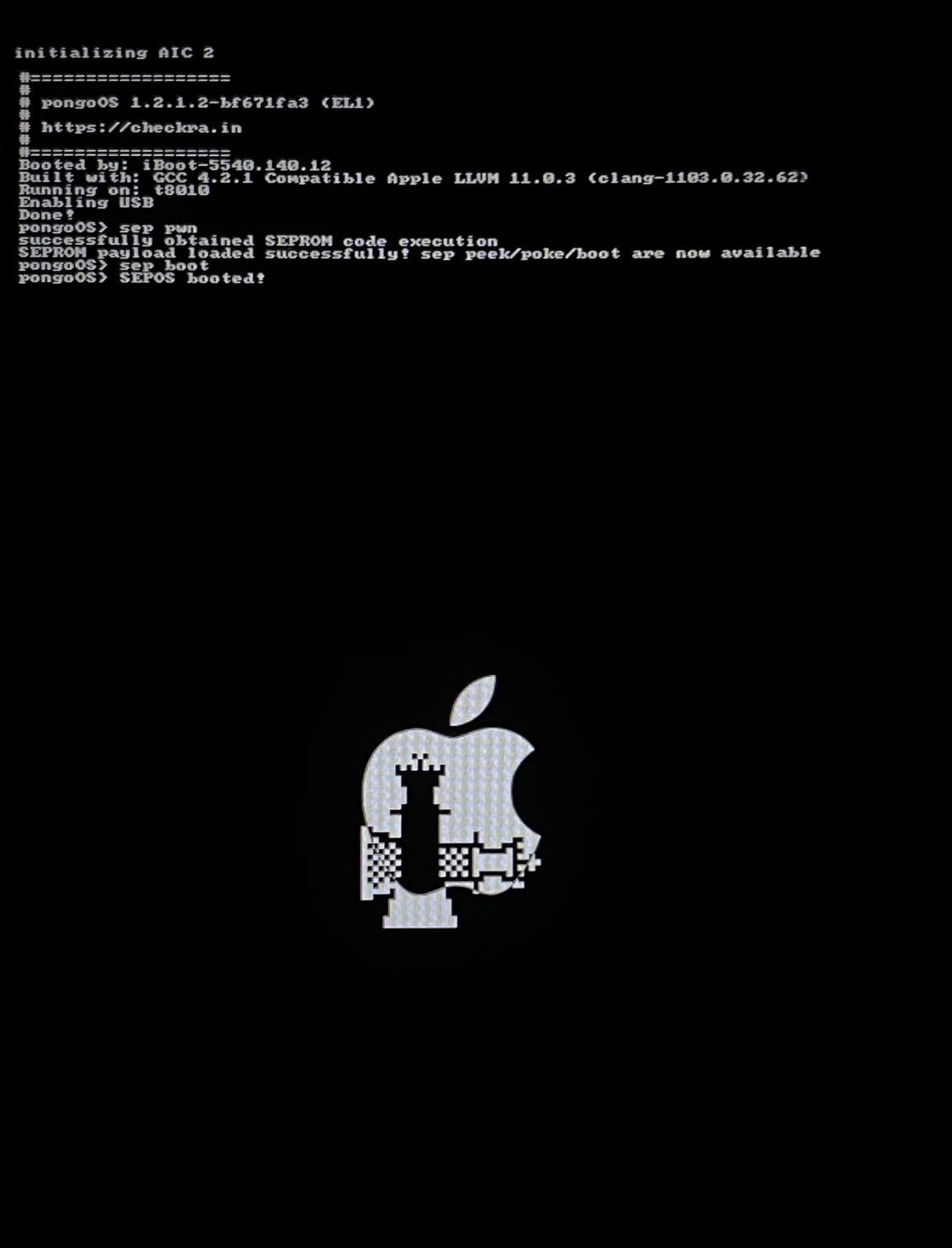
Nearing the end of last month, the Pangu Team took the stage at MOSEC 2020 to discuss a plethora of interesting topics, one of which really stood out from the rest. We’re of course talking about the unpatchable hardware based SEPROM vulnerability that targets a device’s secure enclave processor (SEP).
It wasn’t long after the SEPROM vulnerability was discovered and notes about it were published that famous hackers like Luca Todesco of the checkra1n team began tinkering with it. In fact, it was only yesterday that Todesco Tweeted some particularly eye-catching photos of checkra1n integration on an iOS device and of a T2-equipped Mac running the vulnerability as shown by the Touch Bar’s OLED display:
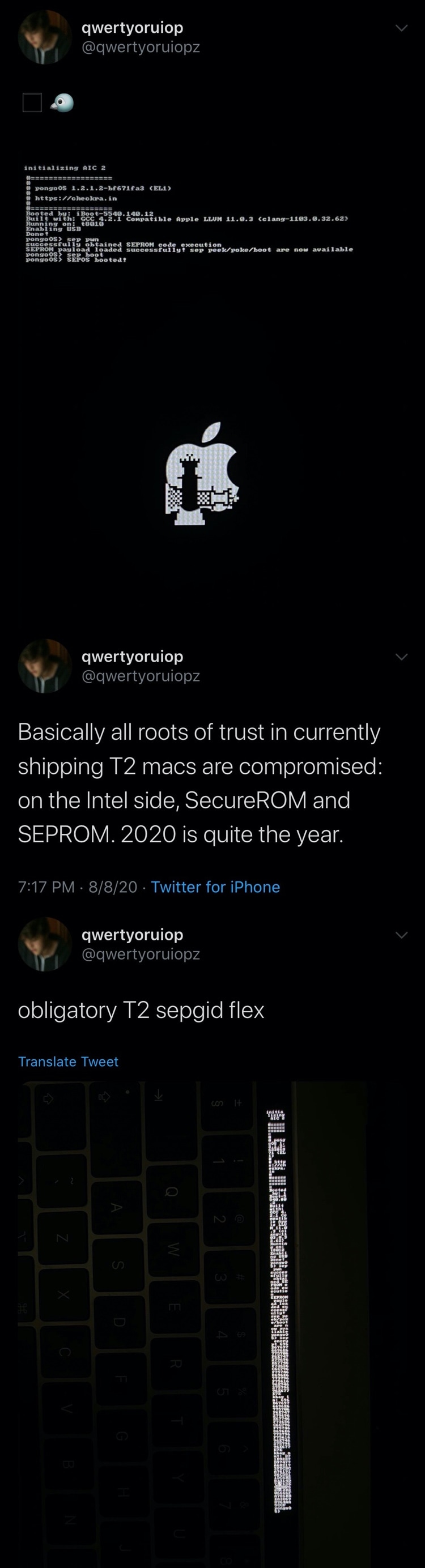
According to Todesco, “all roots of trust in currently shipping T2 Macs are compromised.” But we knew this already because Todesco has been hacking the Mac’s T2 chip for quite some time now.
Adding fuel to the existing fire, Intel-equipped Macs now have SecureROM and SEPROM exploits to contend with, effectively handing full control of any modern Mac back to any user who is able to harness these exploits, as security researcher Will Strafach noted:
The potential ramifications are also evident. A fully compromised security system that was designed by Apple to keep information safe could and would allow a hacker to do basically whatever they wanted with a vulnerable machine’s data.
It’s particularly thought-provoking to witness that so much of Apple’s modern hardware is being compromised by the same people who created and shipped jailbreak tools for much of us to enjoy. It will also be interesting to see what kinds of things may come out of this, potentially to benefit the end users of these machines.
Obviously, it’s a double-edged sword because the same vulnerabilities could be used to benefit malicious intent. That said, Apple will be compelled to deliver an updated security system for its lineup of Macs in the future and it will be interesting to see how they respond.
Are you excited to see what happens next? Let us know in the comments section below.