
The checkra1n team is best known for its checkm8 bootrom exploit-based jailbreak tool for A9-A11 devices. But those closely following outspoken members of the team on Twitter, namely Luca Todesco (@qwertyoruiopz), likely took note of some particularly interesting teasers Tweeted Tuesday morning and afternoon.
A series of images shared by Todesco himself appear to depict checkra1n-centric hacks being deployed and displayed on a MacBook Pro’s OLED Touch Bar:
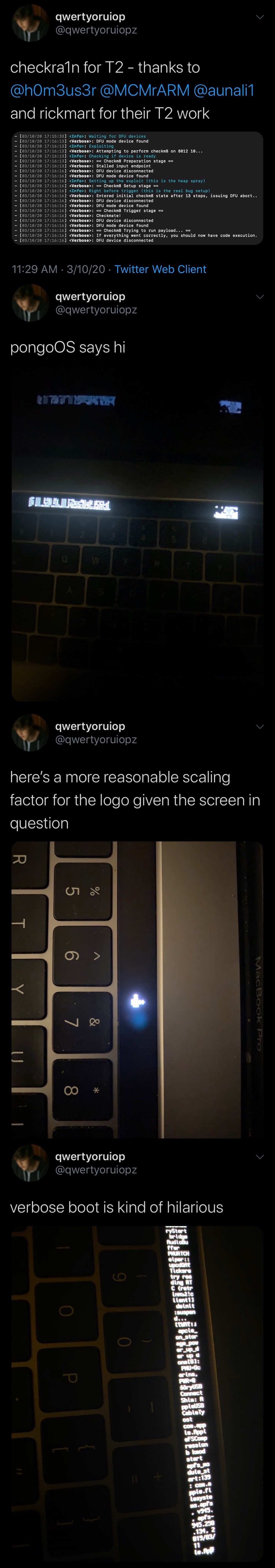
In the first Tweet, Todesco mentions that the hacks are compatible with T2-equipped Macs. Furthermore, he credits others for their help in making the hacks possible, including @h0m3us3r, @MCMrARM, @aunali1, and @almightylinuxgo.
In follow-up Tweets, Todesco shares a plethora of quirky pictures of the MacBook Pro’s OLED Touch Bar displaying various hacks, including pongoOS, a scaled checkra1n icon, and even the text that would be exhibited during a verbose boot.
From what we can gather, these hacks support Macs sporting the T2 chip, but it isn’t yet clear if Macs sporting the older T1 chip would also be vulnerable.
It’s worth noting that a Mac’s T2 chip manages the computer’s security in terms of its secure enclave, which encompasses Touch ID authentication, encrypted SSD storage, and secure boot-ups, among other things. According to Apple, a Mac’s T2 chip is also responsible for managing its System Management Controller, image signal processor, and SSD controller.
Apple-branded computers that come equipped with the vulnerable T2 chip include:
- iMac Pro
- Mac Pro (2019)
- Mac Mini (2018)
- MacBook Air (2018 and later)
- MacBook Pro (2018 and later)
In response to a commenter who asked if they’d be able to jailbreak their Mac, Todesco merely replied with the taunting “eta son” meme.
It remains to be seen what types of benefits someone might gain from hacking their T2-equipped Mac, but given just how much of our lives are stored on our computers these days, it’s also worth mentioning that such hacks could potentially impose security implications. The crucial types of information that a Mac’s T2 chip handles only reaffirms this concern.
There’s no question that Apple will respond to this with an upgraded T3 chip in future Macs. Checkra1n’s core bootrom exploit can only be patched with a hardware upgrade, so it would be impossible for Apple to patch this with a mere software update.
Are you excited to see what becomes of this novel Mac-centric hacking? Share your thoughts and concerns in the comments section below.