
The first round of iPhone 11, 11 Pro, and 11 Pro Max pre-orders started delivering to antsy customers late this week, with the bulk of those arriving today (Friday, 20th). While most people will use their shiny new device as it comes, a smaller percentage are actively anticipating the idea of jailbreaking it. Fortuitously, such an idea might not be too far out of reach.
Renowned security researcher @iBSparkes purportedly succeeded in deploying a tfp0 exploit on his brand-new A13-equipped handset. The hacker shared his experience via Twitter early this morning:
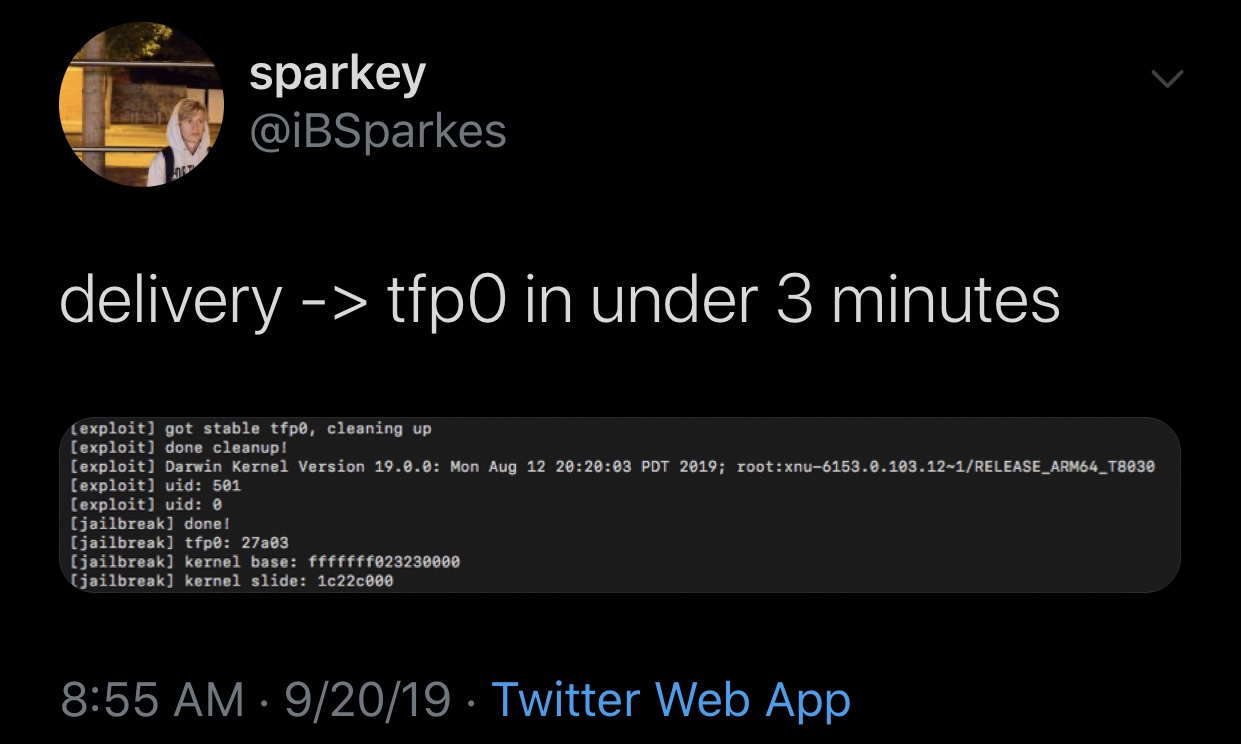
In a somewhat bizarre flex, the hacker claimed that he achieved tfp0 just three minutes after the iPhone delivered. As amazing as this sounds, it’s worth noting that @iBSparkes had this same exploit under his belt for quite some time, originally teasing it at the time of the launch of iOS 13 beta 1 to developers for testing.
As you might come to expect, the tfp0 exploit also supports older handsets, but perhaps more importantly, Apple’s latest and greatest operating system. Since all A13 handsets ship with iOS 13.0, this also means Apple didn’t patch the exploit in any of the betas; on the other hand, with the launch of iOS 13.1 just over the horizon, that could always change.
@iBSparkes never fails to amaze us, but it also remains to be seen if he will release his tfp0 exploit to the public for use in mainstream jailbreak tools such as Chimera or unc0ver or if he will keep it to himself for research purposes.
Whatever the outcome might be, the hacker’s demonstration sheds a positive light for the future of jailbreaking once more because it demonstrates that even Apple’s latest devices aren’t totally pwn-proof. Still, much more is needed than just an exploit to build a jailbreak…
Are you excited to see that Apple’s latest handset is exploitable? Discuss in the comments section below.