Stock, non-jailbroken iOS devices appear to be vulnerable to a new security threat; a trojan known as AceDeceiver, which can be installed on an iOS device without the user’s knowledge and without the help of an enterprise certificate. Once installed, it will spread malware and unwanted software to the user’s device.
AceDeceiver only seems to be affecting those located in China at this point in time, but because that could change on the fly, you need to know how to protect yourself so similar threats don’t affect users across the globe in the future.
How the AceDeceiver iOS trojan works
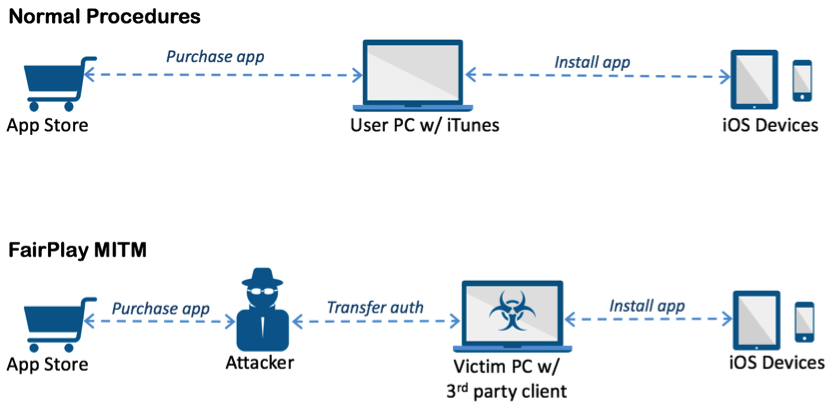
First spotted by Palo Alto Networks, the trojan takes advantage of a vulnerability in Apple’s DRM protection mechanism, known as FairPlay. It’s very much a man-in-the-middle attack and allows software and malware to be installed on iOS devices, purchased or pirated, by tricking the authorization code check that the device uses to confirm with iTunes.
AceDeceiver is the first iOS malware we’ve seen that abuses certain design flaws in Apple’s DRM protection mechanism — namely FairPlay — to install malicious apps on iOS devices regardless of whether they are jailbroken. This technique is called “FairPlay Man-In-The-Middle (MITM)” and has been used since 2013 to spread pirated iOS apps, but this is the first time we’ve seen it used to spread malware. (The FairPlay MITM attack technique was also presented at the USENIX Security Symposium in 2014; however, attacks using this technique are still occurring successfully.)
Apple allows users purchase and download iOS apps from their App Store through the iTunes client running in their computer. They then can use the computers to install the apps onto their iOS devices. iOS devices will request an authorization code for each app installed to prove the app was actually purchased. In the FairPlay MITM attack, attackers purchase an app from App Store then intercept and save the authorization code. They then developed PC software that simulates the iTunes client behaviors, and tricks iOS devices to believe the app was purchased by victim. Therefore, the user can install apps they never actually paid for, and the creator of the software can install potentially malicious apps without the user’s knowledge.
Because the apps can be installed by way of the bogus authentication without user consent, those affected by the trojan are in danger of having their personal data, such as their Apple ID login information, snooped on or stolen.
It’s explained that there were originally three “wallpaper” apps in the App Store between July of 2015 and February of 2016 that managed to pass Apple’s review process and allowed the attackers to obtain a copy of Apple’s DRM authorization code.
Despite Apple removing these malicious apps from the App Store in February, iOS devices remain in danger for their security because the vulnerability still hasn’t been patched in Apple’s DRM protection mechanism and the attackers still have a copy of that authorization code that can be used to install malicious apps.
How it affects users
Users of the infected apps are prompted to install an app on their Windows (not Mac) machines known as Aisi Helper, which claims to be a useful piece of software that could help with restoring devices, jailbreaking them, backing them up, or even cleaning out junk files from them.
Regardless of what it said it would do, Aisi Helper would actually contact a third-party app store that was being controlled by a third-party. It would then enable the attackers behind the third-party app store to use the DRM authorization code they obtained from the official App Store to install malware and apps on the user’s device over the USB connection to the Windows PC without their knowledge.
Specifically, Aisi Helper would automatically install a very specific app onto the iOS device that was tailored to the attackers’ needs, and would ask the user to enter their Apple ID login information to enable more features within the app. These Apple IDs would later be phoned back home to the attackers to keep for their records. This, of course, meant that users Apple IDs were being compromised by the malware.
Who’s still affected?
Although the affected App Store apps have been pulled by Apple, since the attackers already have the DRM authentication code they needed, anyone based out of specific regions in China who downloads the Aisi Helper app on their Windows machine is vulnerable to the trojan.
Again, although it seems to only be affecting some people in certain regions of China, the attackers could always modify their app to affect others anywhere else in the world until Apple officially fixes the DRM vulnerability that the attackers are exploiting.
How to protect yourself
If you use a Windows machine, avoid downloading sketchy software. If you downloaded Aisi Helper, remove it immediately. Those with Macs will be unable to run the Aisi Helper tool, but there’s no telling whether or not this could change in the future.
If prompted to enter your Apple ID for any reason, ensure that you’re entering it into a legitimate Apple app only, and never for a third-party app. Due to App Store restrictions, a third-party app should never ask for access to your Apple ID, so any third-party app asking for it should throw up red flags for you immediately.
Other steps to take, as recommended by Palo Alto Networks, include:
- Check to make sure no strange enterprise certificates have been installed on your device
- Check to make sure no strange provisioning profiles have been installed on your device
- Enable two-factor authentication for your Apple ID
- Change your Apple ID password as soon as possible
The security firm also notes that any enterprise certificates or provisioning profiles related to AceDeceiver could have names equal or similar to:
- aisi.aisiring
- aswallpaper.mito
- i4.picture
Wrapping up
Another day, another vulnerability. Fortunately, by following Palo Alto Networks’ recommendations above, you can help keep yourself safe from this or similar attacks that may exist. Sometimes there is no way to tell if there are other rogue attacks out there like this one until it’s too late.
Will you be taking additional security measures to protect your Apple ID? Share in the comments!
Source: Palo Alto Networks via Mac Rumors