Just as all the hoopla surrounding the XcodeGhost attack appears to have died down, security researchers over at Palo Alto Networks have identified a new type of harmful malware.
Dubbed YiSpecter, it can install itself on both jailbroken and non-jailbroken iOS devices and is the first iOS malware that exploit Apple’s private APIs to implement malicious functionalities.
Here’s everything you need to know about this new type of attack, what Apple is saying about the malware and what you can do in order to protect your devices from becoming infected with YiSpecter.
When was it discovered?
Probably as early as in January 2015, as the malware has been in the wild for over ten months. Out of 57 security vendors in VirusTotal, only one is detecting the malware, as per Palo Alto Networks.
How does YiSpecter spread?
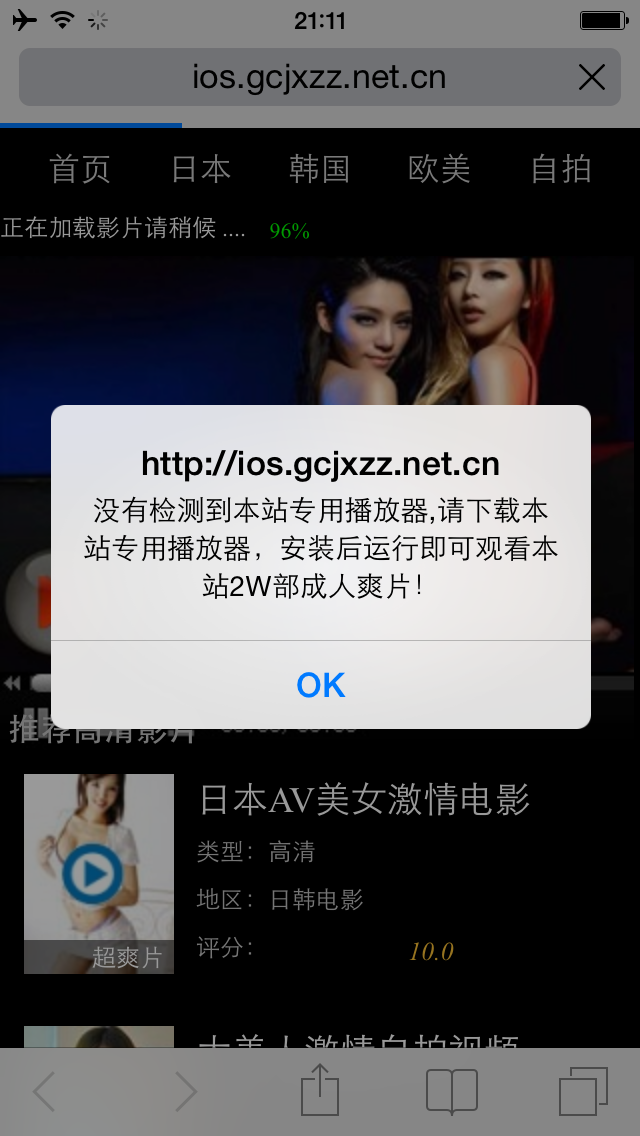
YiSpecter spreads via the usual social network engineering tricks and phishing scams, including some rather unusual means such as the hijacking of traffic from nationwide Internet Service Providers (ISPs), an SNS worm on Windows and an offline app installation and community promotion.
Does it install silently?
Thankfully, no. Because the malware is signed with an enterprise provisioning profile, the user must accept its installation.
Who is affected?
YiSpecter primarily affects iOS-toting users in mainland China and Taiwan.
How can I tell if my iOS device is infected?
On iOS devices infected with YiSpecter, jailbroken or not, you will observe some strange behavior. For example, when you launch an app it might show a full screen advertisement. And if you use file-browsing tools, you can notice some odd “system apps” on infected devices.
What can it do?
Once your device is infected, YiSpecter can download, install and launch arbitrary apps. It can also replace existing apps with those it downloads, hijack other apps’ execution to display advertisements, change Safari’s default search engine, bookmarks and opened pages, as well as upload device information to the C2 server.
Can I manually delete this malware?
Even if you manually delete YiSpecter, it’ll automatically re-appear.
Which apps are affected?
At the time of this writing, more than a hundred iPhone, iPod touch and iPad applications in the App Store were apparently infected with YiSpecter.
How can I protect myself?
First and foremost, update to iOS 8.4 or later, because iOS 8.4, iOS 9.0 and iOS 9.0.1 have already dealt with this threat. People on an older version of iOS that have also downloaded content from untrusted sources have reasons to worry.
The usual caveats apply: make sure you don’t download software from untrusted developers outside the App Store and don’t side-load said apps to your device. Avoid in-app offers which promise incentives to install special apps on your phones, supposedly for tech support folks.
Most importantly, if an app is asking for your permission to install an enterprise provisioning profile think twice before granting it.
What is Apple saying?
Apple issued a statement to The Loop commenting on the new malware threat.
This issue only impacts users on older versions of iOS who have also downloaded malware from untrusted sources. We addressed this specific issue in iOS 8.4 and we have also blocked the identified apps that distribute this malware.
We encourage customers to stay current with the latest version of iOS for the latest security updates. We also encourage them to only download from trusted sources like the App Store and pay attention to any warnings as they download apps.
So, if you have iOS 8.4 installed which has the necessary safeguards in place, and you download apps strictly from the App Store, you’re on the safe side.
And now the good news…
According to Mac security expert, Thomas Reed, director of Mac Offerings at Malwarebytes, YiSpecter does exhibit some fairly unique behaviors but it still is “no more able to install itself invisibly than any other iOS malware to date.”
“Two aspects of this are concerning,” Reed told me via email. “One is the difficulty of removing the malware – I’d recommend a full factory reset of the phone to be 100% sure everything is wiped.”
“Second is the wide variety of ways this malware has been spread, including incentives to get repair techs and the like to install it on phones they ‘fix,’ and the hacking of ISP-injected advertising,” he continued.
While the hijacking of traffic from ISPs, an offline app installation and community promotion are fairly common malware spreading techniques in China and Taiwan, in places like North America or Western Europe these techniques are unlikely to yield results due to tight controls in place to prevent this type of activity.
“Still, that’s of no help to people in China who are affected by this,” said Reed.
“This attack is complicated by the fact that there’s no anti-malware software for iOS, and no way for any software to scan iOS due to sandboxing restrictions.”
Source: Palo Alto Networks