A new exploit in the Bash command shell found in many versions of Unix, including Apple’s OS X desktop operating system, makes Mac computers vulnerable to so-called ‘Shell Shock’ attacks, security researchers at RedHat discovered Thursday.
Though the exploit lets attackers run malicious scripts remotely, most people are not at risk unless they’ve manually allowed SSH access from remote connections or a web server running server side scripting.
Here’s how you can check if you’re vulnerable and what you can do in order to avoid ‘Shell Shock’ attacks on your system.
“You are only truly vulnerable if someone you do not know can remotely access your machine and do so in a way where a Bash command can be executed,” researchers explained.
A thread on Stack Exchange explains that determining whether or not your Mac is prone to Shell Shock attacks involves running the following command in Terminal (found inside your Mac’s Applications folder):
env x='() { :;}; echo vulnerable' bash -c 'echo hello'
If the word ‘vulnerable’ gets printed in the Terminal window after running the above command, your system is exploitable.
If it says:
bash: warning: x: ignoring function definition attempt
bash: error importing function definition for `x’
hello
then you are good.
The adventurous types who have Apple’s Xcode and the command-line compilers installed can fix the issue on their own by compiling a new, patched Bash version.
Be warned that the process is not for the faint-hearted. If you feel like giving it a shot, follow the full instructions in the linked Stack Exchange thread.
Security researcher Robert Graham wrote on his blog that the Bash exploit is “as big as the Heartbleed bug” which was discovered earlier this year in the commonly used OpenSSL software used by web servers.
Because the Bash vulnerability has been around for a long time, there are lots of old devices on the network vulnerable to this bug. “The number of systems needing to be patched, but which won’t be, is much larger than Heartbleed,” Graham wrote.
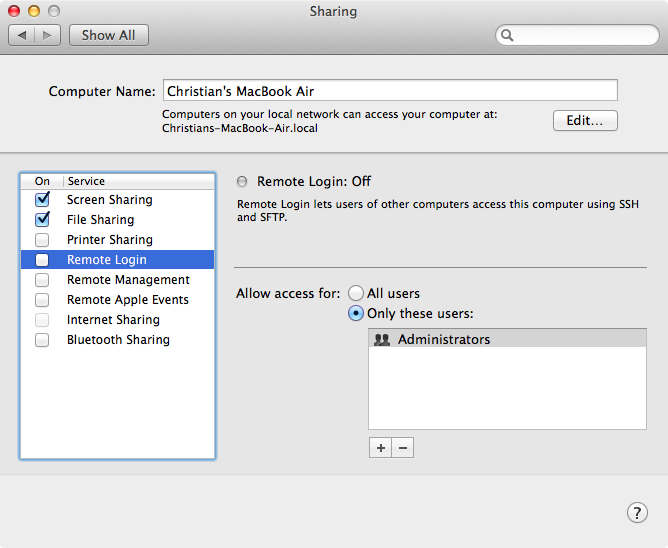
Disable Remote Login in System Preferences, just in case.
Again, the vulnerability should mainly concern system administrators on Mac OS X, Unix and Linux servers exposed to the world rather than desktop users, the vast majority of whom never enable SSH sharing in System Preferences.
Apple’s latest OS X Mavericks 10.9.5, which was released last week, does not include a fix for the Bash vulnerability. As several variants of Linux already have patches available, chances are Apple is going to soon put out a fix for OS X to address the exploit.
At any rate, we’ll keep you posted.