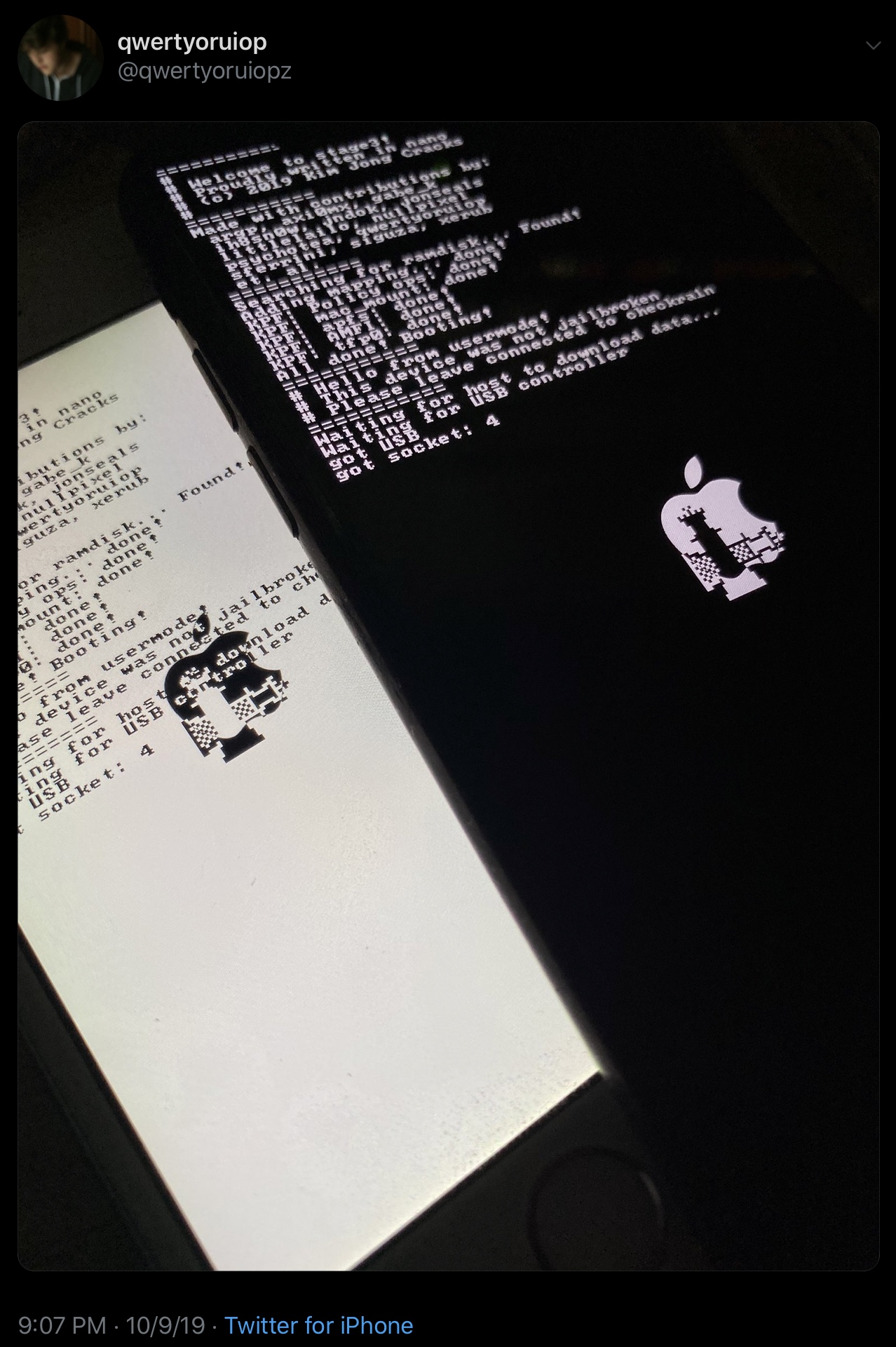
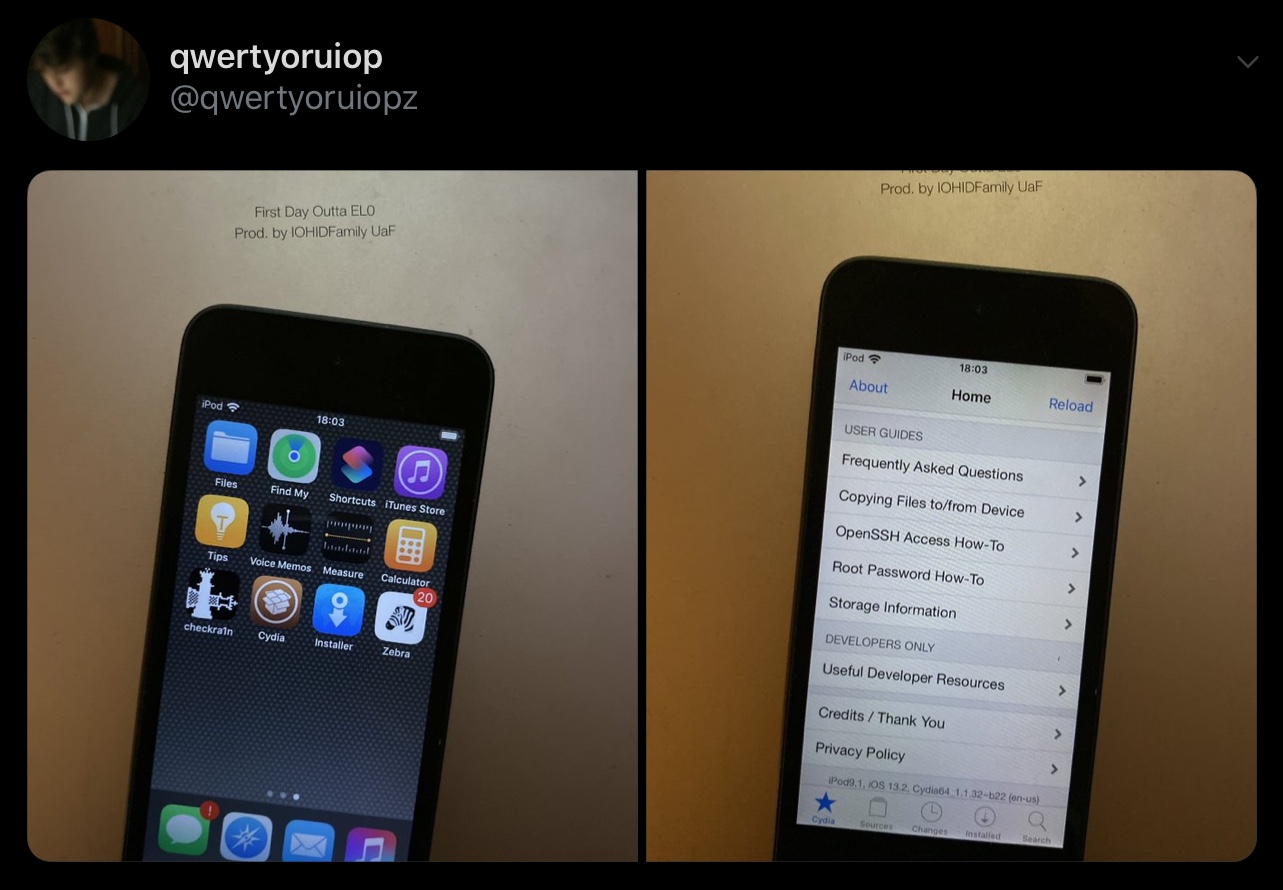
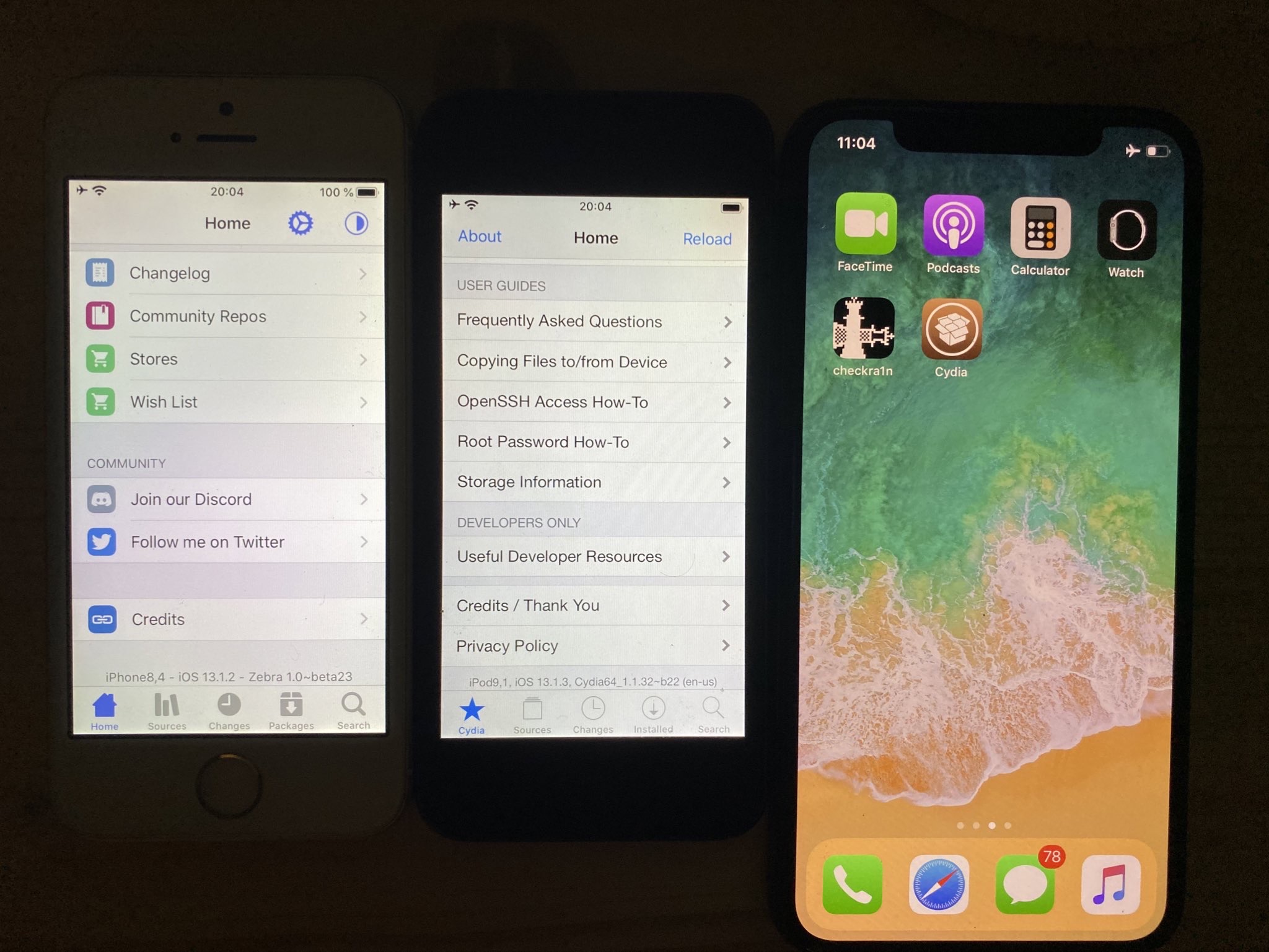
Not even 24 hours after the initial public beta release of the checkm8 exploit-based checkra1n jailbreak tool, the checkra1n team has already launched its first bug fix update dubbed v0.9.1.
The newest version of checkra1n was announced only minutes ago via the checkra1n team’s official Twitter account: