
Timely security patches and seamless iOS software updates are among the chief reasons for many Android customers to switch to an iPhone.
However, a new survey has discovered something potentially disturbing.
Wired today cited German security firm Security Research Lab which has discovered that many Android vendors are lying to customers about important OS security patches by changing the security update date on the device without actually installing any patches.
It is no secret that Google has long struggled with getting OEMs and carriers to regularly push out security patches for Android.
Having spent two years analyzing Android updates, the company has discovered that many Android OEMs fail to make patches available to their users, or delay their release for months.
And in some cases, vendors tell users their phone’s firmware is fully up to date even though they’ve secretly skipped patches. “We found several vendors that didn’t install a single patch but changed the patch date forward by several months,” says researchers Karsten Nohl.
“That’s deliberate deception, and it’s not very common.”
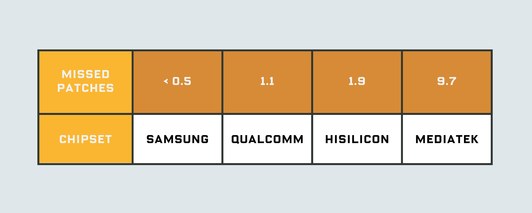
Android security patches via Security Research Lab and Wired
Some of the missing patches can be blamed on phones with chips by MediaTek and Qualcomm, the former lacking 9.7 patches and the latter 1.1 patches on average. When bugs are found in these chips rather than in Android itself, the phone manufacturer depends on the chipmaker to offer a patch.
“The lesson is that if you go for a cheaper device, you end up in a less well maintained part to this ecosystem,” Nohl added.
Google responding by saying that some of the smartphones that Security Research Lab analyzed may not have been Android-certified devices, but underscored it’s working with the researchers to further investigate their findings.
According to Scott Roberts, Android’s product security lead:
Security updates are one of many layers used to protect Android devices and users. Built-in platform protections, such as application sandboxing, and security services, such as Google Play Protect, are just as important. These layers of security—combined with the tremendous diversity of the Android ecosystem—contribute to the researchers
Google claims that modern, Android-certified devices include security capabilities which make them difficult to hack even when they do have unpatched security vulnerabilities.
According to the search giant, in some cases security patches might have been missing from devices because their vendors may have removed a vulnerable feature from the phone rather than patch it, or the phone didn’t have that feature in the first place.
Security Research Lab will present their full findings at an event in Amsterdam.