We’ve seen a spate of jailbreak tool releases of late for both iOS 10 and iOS 11. I’ve covered their current statuses and differences in a previous article, but today we’ll take a more specific look at the 64-bit iOS 10.3.x option, g0blin, by sticktron.
32-bit devices on iOS 10.x are catered for by a different tool, h3lix by tihmstar, and can expect to use that for the rest of their miserable lives.
The g0blin tool has been cleverly stitched together by sticktron using various existent pieces, including:
- The v0rtex kernel exploit by Siguza, itself built on a vulnerability discovered by Ian Beer
- The KPP bypass, sandbox, and codesigning from Luca Todesco’s Yalu102
- Additional sandbox patches from h3lix by tihmstar
- The patchfinder from Xerub’s extra_recipe
- Additional patchfinder work from async_wake_fun by ninjaprawn
The vulnerability (though not the kernel exploit) is the same as the one powering iOS 11’s jailbreaks, Electra and LiberiOS. The KPP bypass from Yalu102 which g0blin uses makes it a traditional jailbreak, without a jailbreak daemon, compatible out of the box with Cydia Substrate and its dependencies, and bundled with Cydia. For more information on this topic, check out my comparative article on current jailbreaks. Whilst the KPP bypass allows for easy Cydia compatibility, it only works up to iOS 10.3.3, and only on A7-A9 devices. For this reason, it can’t be used in the iOS 11 tools. In addition, it means A10 and A10X devices are not supported by g0blin for iOS 10.3.x.
These unsupported devices are:
- iPhone 7
- iPhone 7 Plus
- 10.5″ iPad Pro
- 12.9″ iPad Pro (2017)
The KPP bypass also introduces some unreliability into the jailbreaking process, which may fail several times before succeeding. This is on par with the Yalu and extra_recipe jailbreaks, and is avoided by the KPP-less iOS 11 jailbreaks.
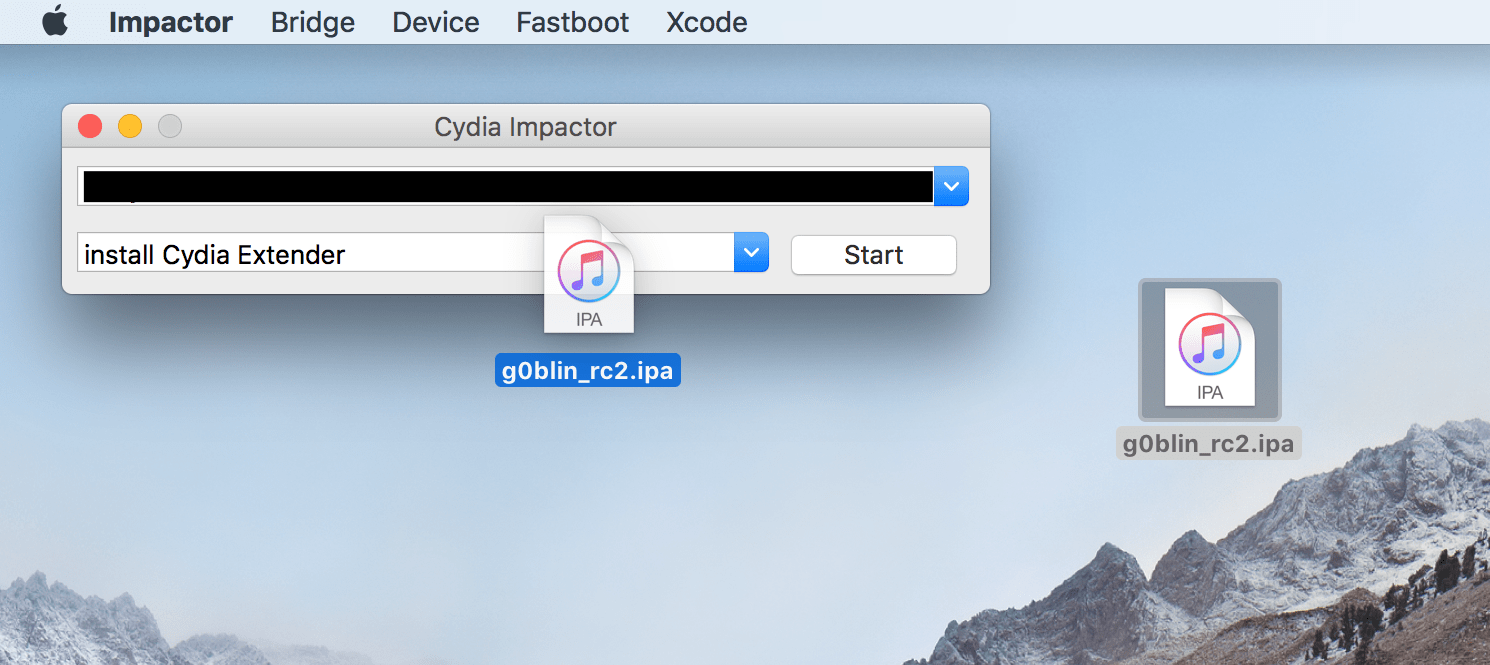
I tested g0blin Release Candidate 2 on an iPhone 6 on iOS 10.3.1, as shown below. Sideload the app onto your device using Cydia Impactor, the same as with all recent jailbreaks.
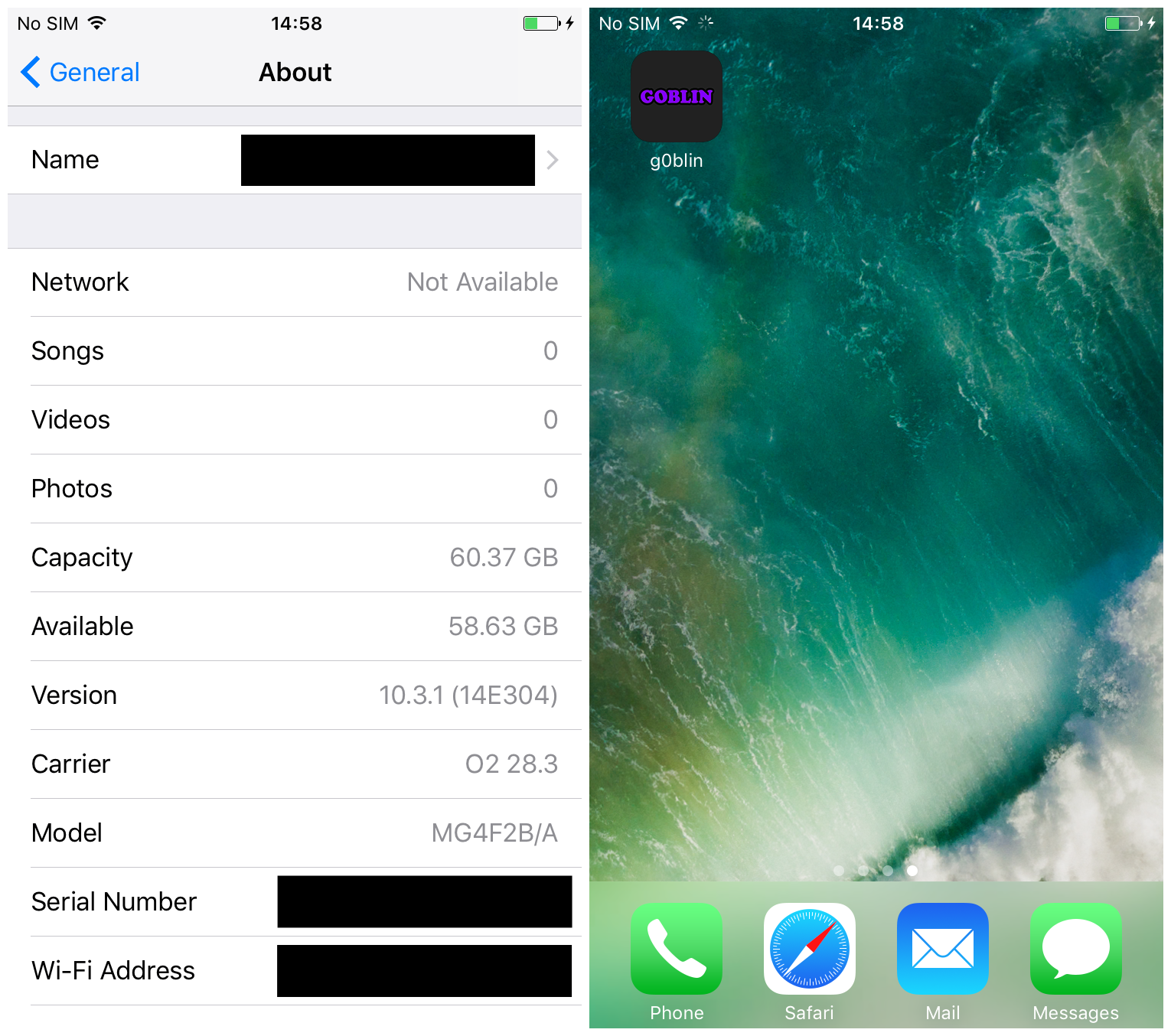
Once the app appears on your device, head to Settings, Profiles & Device Management and Trust the app. You can now launch it from your Home Screen.
The images below show the g0blin interface. The left-hand image is the main interface, which displays the revision of the app you are running, various system informations, and the jailbreak button. The right-hand image shows the credits screen, which also includes an option to force re-install Cydia in the case of problems.
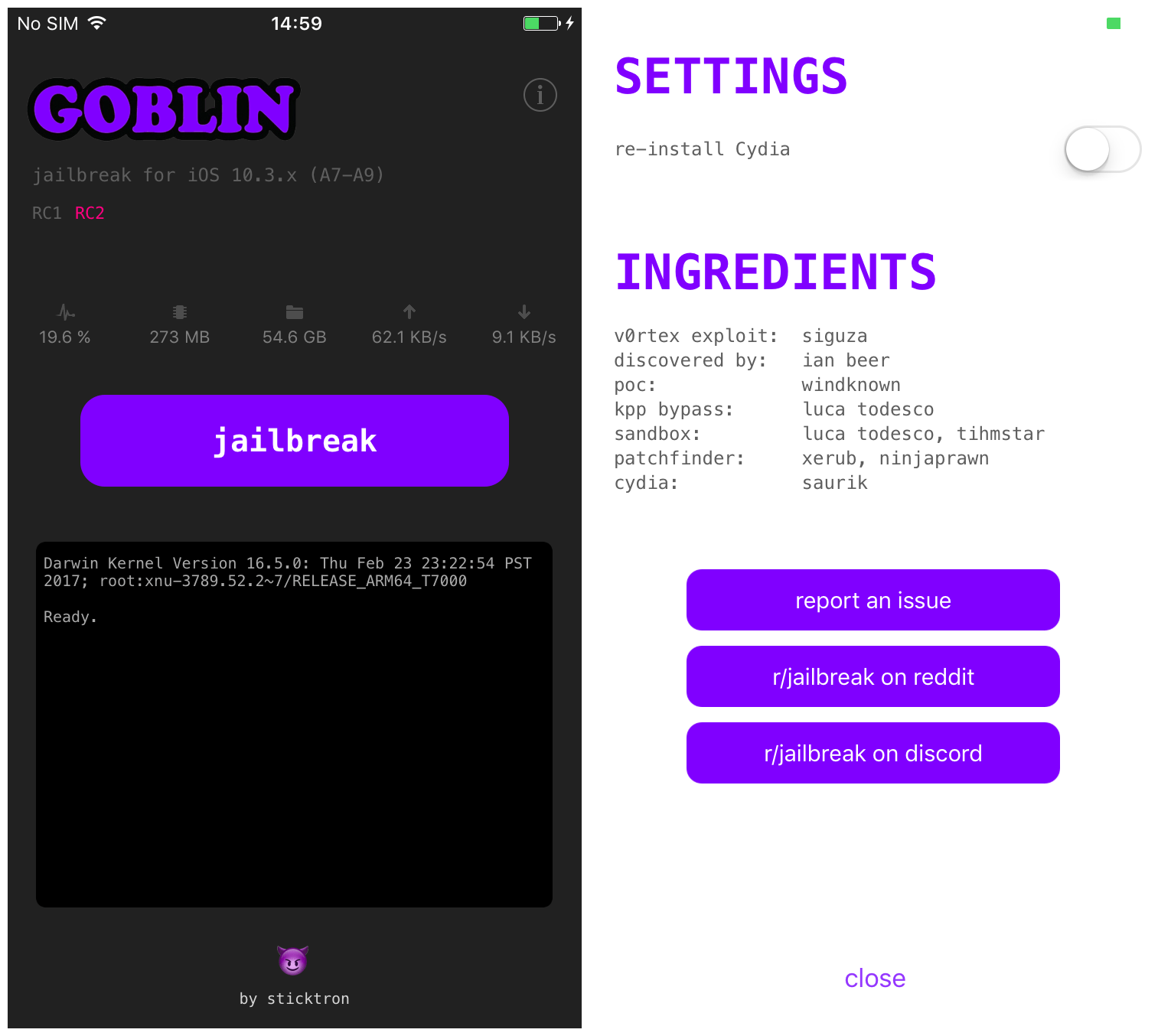
To jailbreak, simply tap the jailbreak button. The readout in the black box below will tell you if it’s been successful. If it fails, reboot your device and try again until it succeeds.
The first time you run it, the app will install Cydia to your system as part of the jailbreak process. Once jailbroken, the app displays the screen below, with a cheery jailbroke yo! into the bargain.
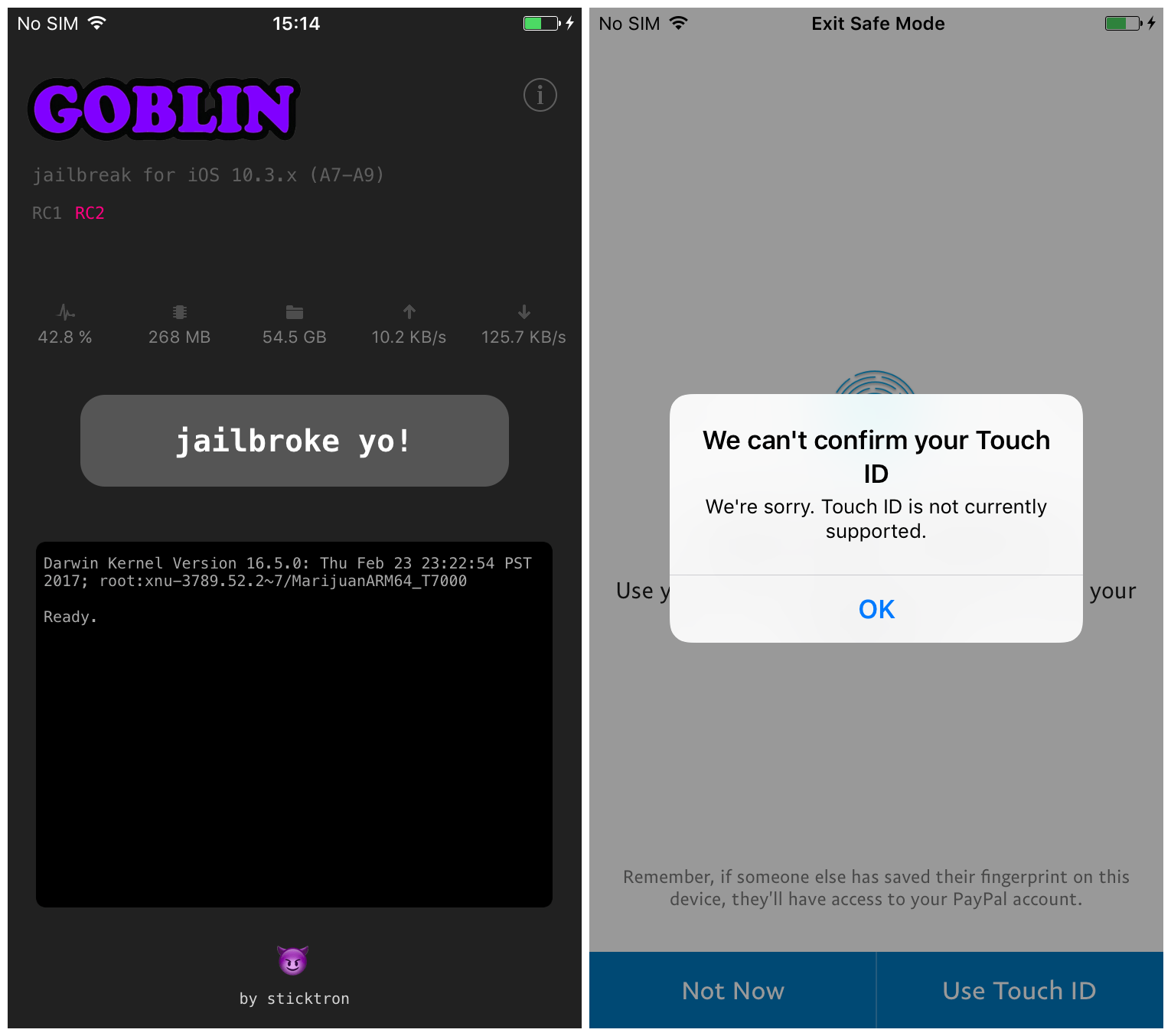
As you can see in the right-hand image above, g0blin currently has a known issue whereby Touch ID is non-functional in third-party apps whilst jailbroken. Stock Apple apps are unaffected by the bug, and rebooting to an unjailbroken state allows Touch ID to function again with no ill effects. Hopefully RC3 will include a fix for this issue, which can be irritating on a daily driver, due to many banking and shopping apps using Touch ID instead of a lengthy login process.
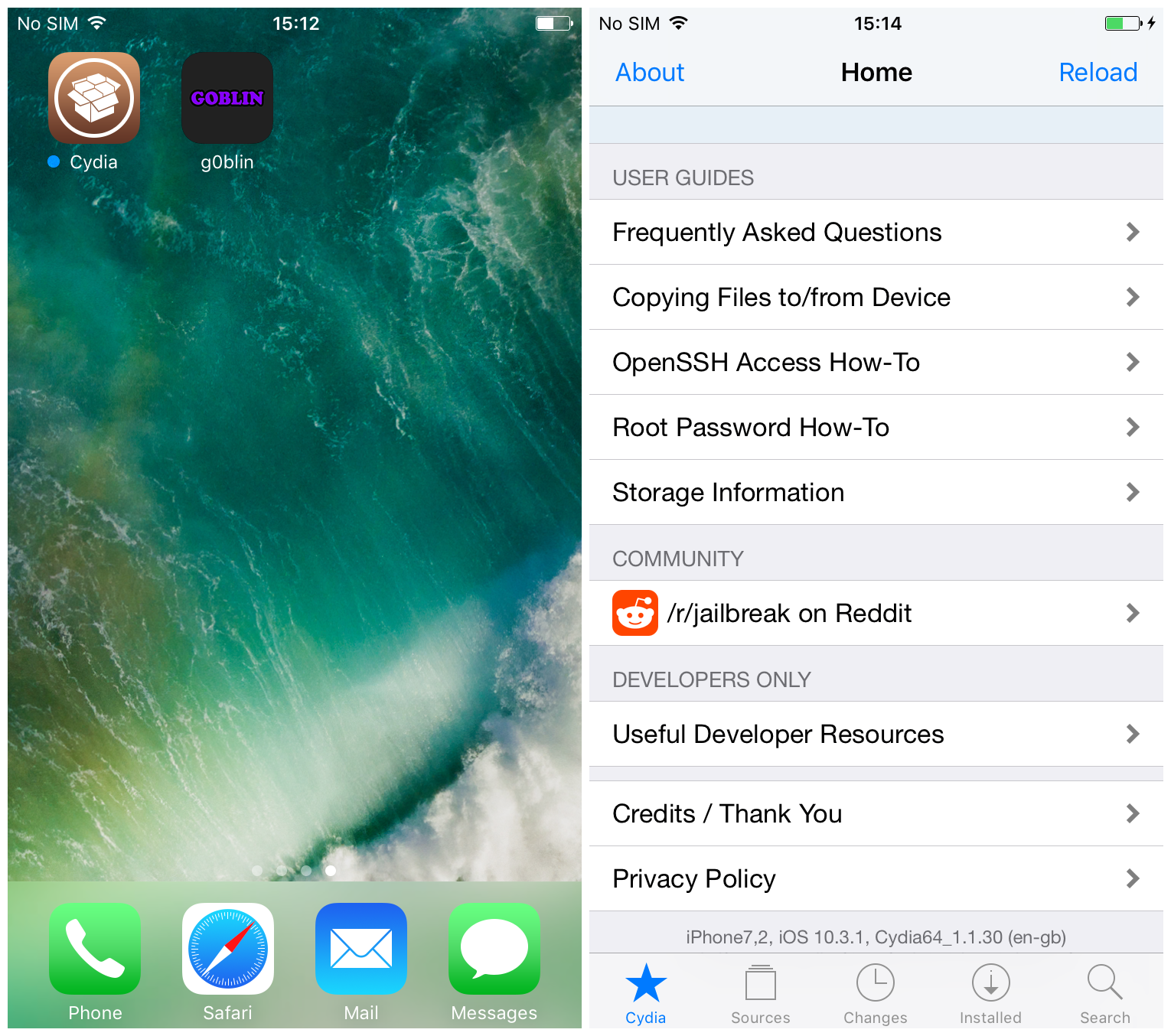
Once jailbroken, you can launch Cydia from the Home Screen, as shown above. As g0blin includes a working Substrate all your tweaks should work as expected, provided they are compatible with iOS 10.3.x. Most tweaks work anyway, due to relatively few changes between iOS 10.2 (which has had a jailbreak for a long time) and iOS 10.3.x.
I have so far found g0blin very stable once jailbroken. The initial exploit can take a few attempts to run, but is nowhere near as tricky as extra_recipe on my iPhone 7 on iOS 10.1.1. It generally succeeds within the first five tries in my experience. Once the Touch ID bug is fixed g0blin will be a fully functional tool, with no downsides to its use. It should also allow users who have waited on iOS 10.3.x to jailbreak, set a nonce, and then futurerestore to iOS 11 if they like, in order to re-jailbreak there with Electra or LiberiOS. This will of course require saved blobs.
Have you tried out g0blin yet? How have you found it?