I download apps for my Mac from the Mac App Store whenever possible. Going through the Mac App Store gives me a piece of mind knowing Apple screens all submissions and keeps harmful software at bay.
But every once in a while, an app comes along and gets distributed outside the Mac App Store’s safe haven. True, one can verify signing information for non-Mac App Store apps in Terminal, but it isn’t for the faint-hearted.
That’s precisely the kind of problem that a nifty little Mac app, called Suspicious Package, solves in one fell swoop.
Created by a company called Mothers Ruin Software, the free of charge app is actually a plug-in for the Mac’s Quick Look feature, allowing you to easily and quickly inspect contents of a .PKG installer file after you’ve downloaded it but before it’s launched.
Upon downloading Suspicious Package to your Mac, double click the installer to deploy the Quick Look plug-in on your system. Depending on your Mac’s security settings, you might be prompted that the app cannot be installed.
Should you encounter this message, right-click the installer file, choose Open from the contextual menu and confirm that you wish to install Suspicious Package.
Quick Look plug-in
In case you’re unfamiliar with Quick Look, it’s an overlooked OS X feature that lets you quickly preview known file types without opening them in creator apps. Third-party developers have long been able to write their own Quick Look plugins for custom file types which are not supported by OS X out of the box.
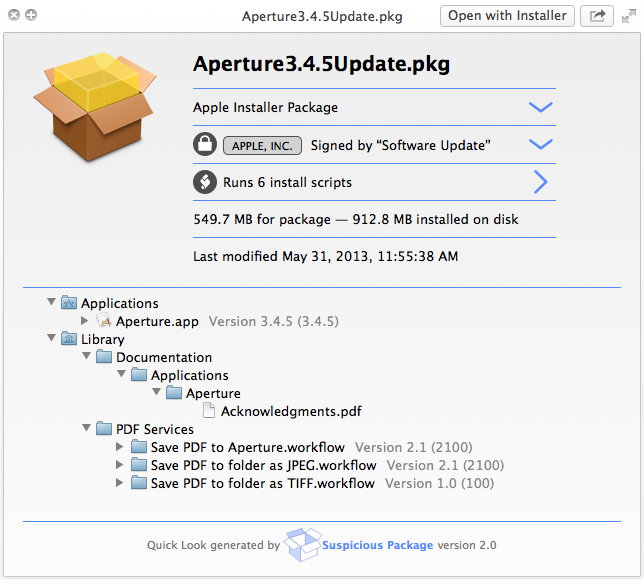
Upon installing Suspicious Package, just select a .pkg installer file in the Finder and press Space on the keyboard. This will bring up a Quick Look preview with various pieces of information pertaining to the contents of the installer, including crucial signing information (more on that in the following section).
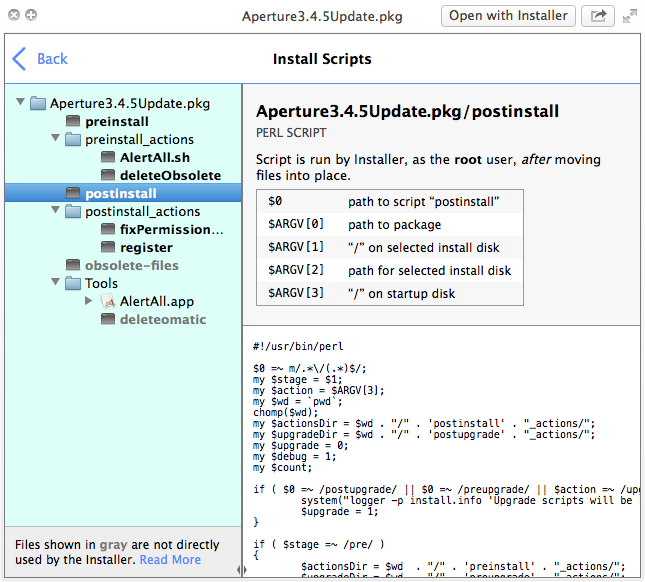
The Quick Look plug-in surfaces all sorts of other information such as an overview of the package’s folder structure and files and detailed information about the underlying installer scripts that are executed by the OS X Installer.
Speaking of installer scripts, know that a “malicious package could take advantage of this mechanism to wreak havoc, and even well-intentioned but buggy packages might do damage,” as per developers.
Pictured above: Suspicious Package’s scripts browser.
Crash course on signing and certificates
If the package was signed with a valid Apple certificate, you will see a valid Developer ID certificate under the Signed By headline. A package can be:
- APPLE, INC.: Signed with a valid Apple certificate for safe software distribution through www.apple.com, OS X Software Update or the Mac App Store.
- DEVELOPER ID: Signed with a valid Developer ID certificate issued by Apple under the Gatekeeper program for safe software distribution outside the Mac App Store.
- VALID: Not certified using an Apple or Developer ID certificate under the Gatekeeper program, but signed with a certificate issued by a certificate authority which is trusted by OS X
- NOT TRUSTED: Signed using a certification not trusted by OS X, nor issued by a trusted certificate authority.
- EXPIRED: Signed with a certificate which has expired or been revoked.
- REVOKED: A certificate could be revoked because it was lost or stolen.
- MARKED AS TRUSTED: Signed with a certificate marked as trusted on this Mac.
Sometimes, OS X’s Installer verifies if a package was signed before the certificate became invalid. In those cases, the OS X Installer will deem the signature valid but the Quick Look preview will flag it as Expired or Revoked because Suspicious Package lacks access to the verified time-of-signing information.
Limitations
For starters, Suspicious Package won’t directly tell you if a package was modified since being signed due to the complexities involved in signature verification.
Next, OS X supports a wide variety of installers and Suspicious Package doesn’t necessarily understand them all. If Quick Look won’t recognize the structure of an installer package, you will see a message saying the package is broken or archaic.
Finally, Suspicious Package might not always show you all of the files if the number of files installed by the package exceeds 10,000 items, which is very rare.
Uninstalling Suspicious Package
Suspicious Package is by default installed for all users, but the installer lets you optionally restrict the Quick Look plug-in to your own user account on the Mac.
To remove the app, open the startup disk in the Finder and trash the item named Suspicious Package.qlgenerator located inside the Library > QuickLook folder. You will need to provide your administrator password to remove the Quick Look plug-in.
More apps like this
If you like Suspicious Package, check out a similar app called Pacifist. This Mac utility gives you complete access to package and installer files and their contents, and can even extract the individual files, without running the installer itself.
You can download Pacific at no charge from the official website and register for $20 a pop if you determine you’ll be using it regularly. Folks concerned about certificate trust and signature validity can also verify a package signature before attempting installation with an OS X tool called pkgutil, from the Terminal.
Wrapping up, I would like to point out that I have found out about Suspicious Package through Dave Mark of The Loop.
Availability
Suspicious Package requires an Intel-based Mac with OS X 10.8 Mountain Lion or later. An older version of Suspicious Package for legacy Macs running OS X 10.7 Lion or OS X 10.6 Snow Leopard is available as well.
As Quick Look was introduced with OS X Leopard, Suspicious Package for older OS X versions is a standalone app rather than a Quick Look plug-in.
Due to sandboxing restrictions, the app is not available through the Mac App Store. For those wondering, the Suspicious Package installer itself is signed with an Apple-issued certificate, meaning it’ll be recognized as valid by OS X’s Gatekeeper feature.
Grab Suspicious Package at no charge from the official website.