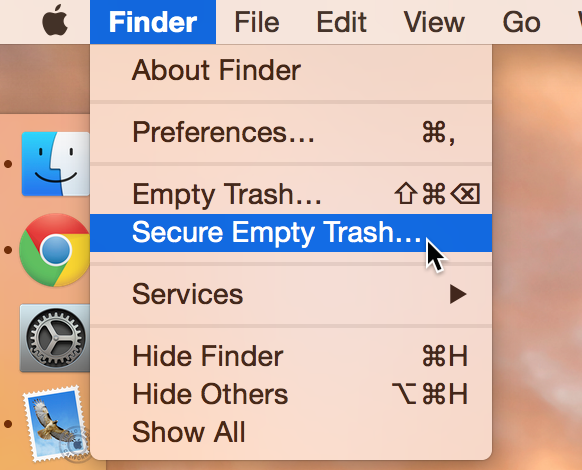
Did you know that there are actually two ways to empty the trash on your Mac? Perhaps you’ve seen both options before, but never gave it much thought. Just what is the deal with Empty Trash versus Secure Empty Trash? Which one should you use? By knowing what each empty trash command is capable of doing, you’ll be able to make more informed future decisions with regard to handling your Mac’s sanitation needs.
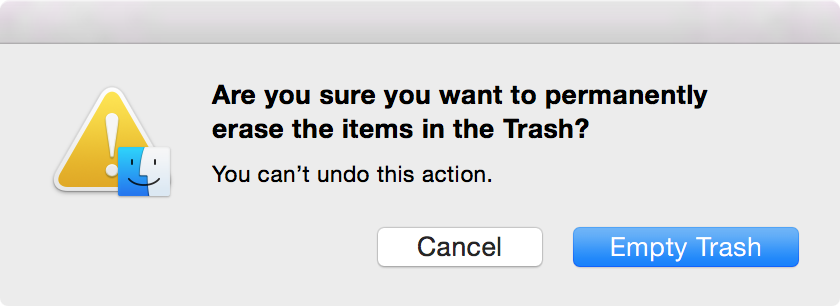
Unsurprisingly, one method of deletion is more secure than the other method of deletion. Performing a standard Empty Trash command will simply mark the deleted files as being available to be overwritten should the need for space occur. The actual file is still there on your hard drive. You can’t see it, but it is there until another file uses the data once designated to it, and therefore it’s easily recoverable by using recovery software.
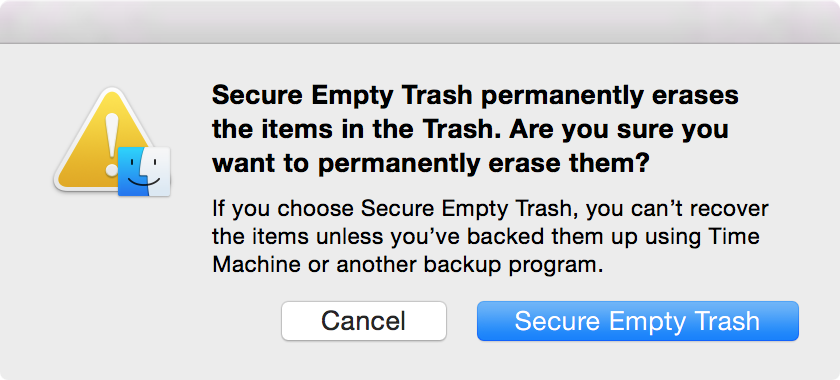
The second, more secure method of deletion—Secure Empty Trash—actually overwrites the deleted file using a single pass erase. So not only are these blocks freed up to accommodate other data, but they’re actually overwritten, and, in theory, less susceptible to recovery. With this in mind, it takes a longer time to Secure Empty Trash since an actual overwrite is being performed.
So which deletion method should you use? I’d say for every day things, it’s safe to continue using the standard Empty Trash command. In contrast, if you’re working with data that has some sort of sensitive element to it, it may be wise to use the Secure Empty Trash command instead.
At any rate, here’s what Apple has to say about the whole thing:
Users can also initiate sanitization while deleting files using the Secure Empty Trash command in the Finder. This command overwrites files as they are deleted using a single-pass erase
Now you’re much better equipped to know which type of delete you should use in the future. But keep in mind that even a Secure Empty Trash would likely leave elements of files lingering around, making them recoverable using forensic software. Drop me a line down in the comments with any further thought you may have on the topic.