Yesterday’s report by Quarkslab, a penetration testing company, has caused quite a stir among privacy watchers as iOS hacker Pod2g and Quarkslab’s team of researchers claimed at the Hack the Box conference in Kuala Lumpur they had successfully intercepted iMessage exchanges, indicating Apple has access to the public keys used to encrypt communication.
Given the ongoing NSA scare, Apple was quick to go on the record to dispute the claim, arguing end-to-end encryption employed to protect eavesdropping on iMessages communication is so secure that even the company itself cannot decrypt it…
John Paczkowski of the well-regarded AllThingsD blog has a written statement contributed to Apple’s spokeswoman Trudy Muller:
iMessage is not architected to allow Apple to read messages. The research discussed theoretical vulnerabilities that would require Apple to re-engineer the iMessage system to exploit it, and Apple has no plans or intentions to do so.
In other words, Apple would need to re-engineer the entire backend powering the iMessage service in order to read your messages.
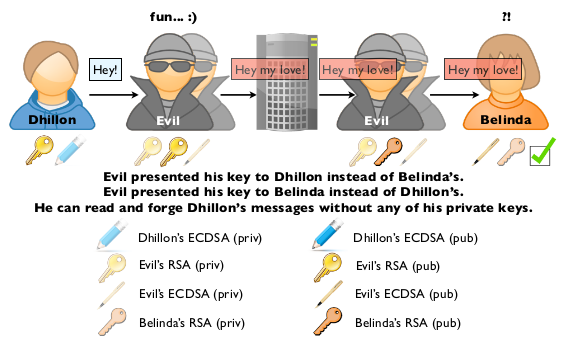
“Apple can read your iMessages if they choose to, or if they are required to do so by a government order,” QuarksLab wrote in its white paper. End-to-end encryption be damned, QuarksLab warns the biggest weakness is in the Apple-controlled key infrastructure.
They posted a video detailing the process, have a look.
“They can change a key anytime they want, thus read the content of our iMessages,” reads the white paper. My take: we’re just going to have to trust the provider – in this instance Apple – that it won’t read our iMessages or give their public key to the government.
With great power comes great responsibility.
If you remember the June report based on data leaked by the NSA whistleblower Edward Snowden, the NSA had apparently teamed up with the biggest names in technology on its PRISM data mining program.
Shortly after the scandal blew up, Apple issued a statement on government information requests, saying it was unable to access or decrypt iMessages.
For example, conversations which take place over iMessage and FaceTime are protected by end-to-end encryption so no one but the sender and receiver can see or read them. Apple cannot decrypt that data. Similarly, we do not store data related to customers’ location, Map searches or Siri requests in any identifiable form.
A report earlier in the year lent the claim an aura of credibility after a leaked memo by the United States Drug Enforcement Administration had cautioned that it was impossible for DEA agents to “intercept iMessages between two Apple devices,” even with a court order approved by a federal judge, due to strong iCloud encryption.
What’s your take?
Is iMessage secure enough for mainstream use and are you concerned about the government reading your message exchanges?
Chime in with your thoughts down in the comments.