Once again, another Lock screen vulnerability has reared its ugly head, this one right on the heels of Apple’s 7.0.2 update to fix another vulnerability.
Dany Lisiansky has posted the steps on a YouTube video he recently uploaded, and we’ve verified that the steps, albeit a bit involved, do work.
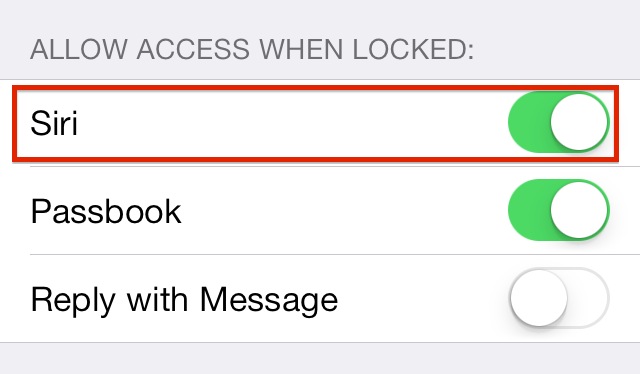
If there’s one bright spot about this latest vulnerability, it is that it doesn’t expose anything outside of the Phone app to would be snoopers, and you can nix the bug by disabling Siri access from the Lock screen. Still, Apple’s security team can’t be happy about this.
You can test the bug out for yourself, as Lisiansky has outlined the steps in the video’s description:
Step 1: Make a phone call (with Siri / Voice Control)
Step 2: Click the FaceTime button
Step 3: When the FaceTime App appears, click the Sleep button
Step 4: Unlock the iPhone
Step 5: Answer and End the FaceTime call at the other end
Step 6: Wait a few seconds
Step 7: Done. You are now in the phone app
This might not seem like that big of a deal, but it’s a big flaw in my opinion. While it’s true that you can only use Siri to dial contacts, this bug allows anyone to see your entire list of contacts, your call history, even your voicemail.
It’s just another case of allowing users to do too much from the Lock screen. Of course, you can go into the Settings > General > Passcode & Fingerprint settings, and disable Siri access from the Lock screen until Apple fixes this issue.
What are your thoughts about Apple’s ongoing Lock screen security issues?